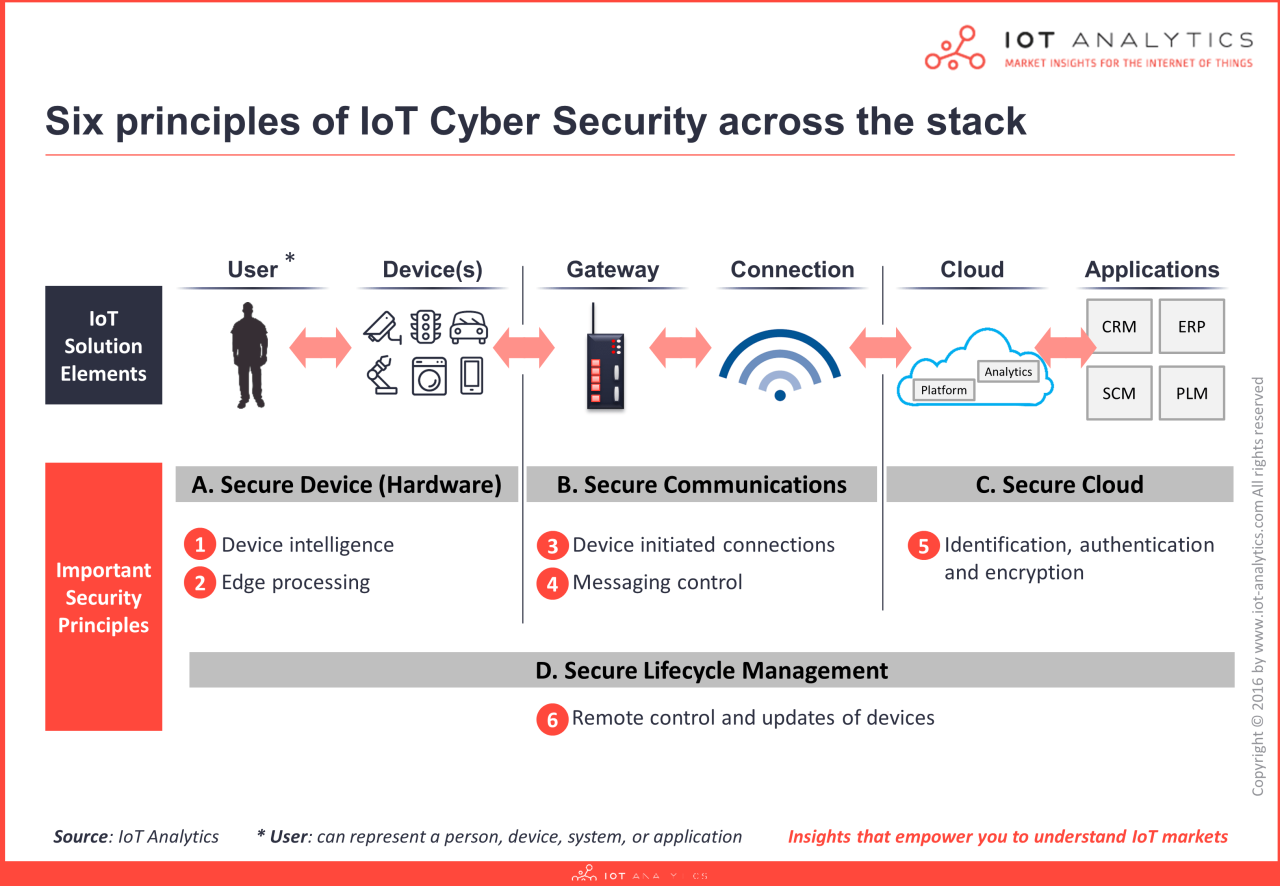
Iot Security Protocols
IoT security protocols play a crucial role in safeguarding data integrity and confidentiality, as well as protecting connected devices from cyber threats. Let’s delve into the world of IoT security protocols and explore their significance.
Overview of IoT Security Protocols
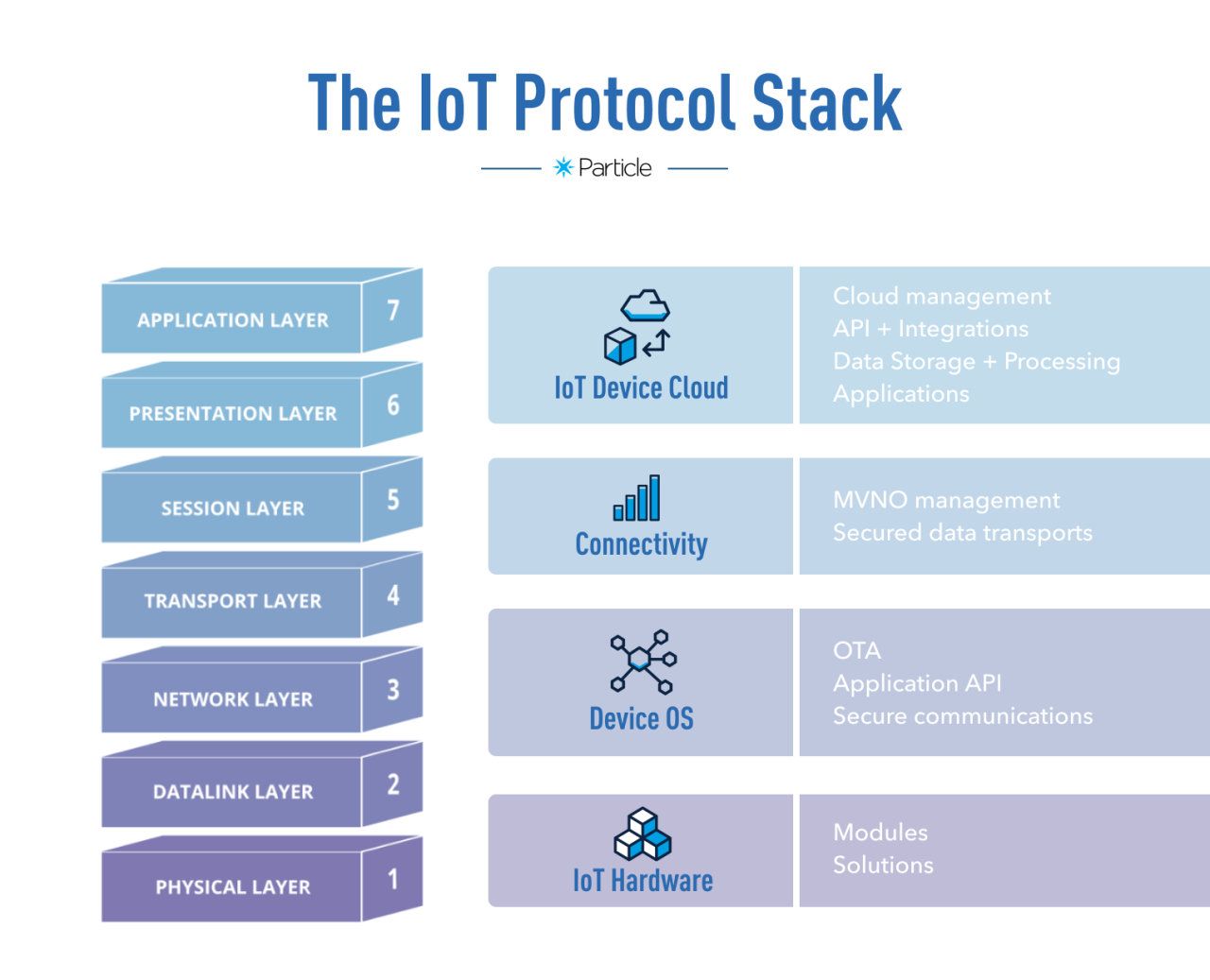
IoT security protocols play a crucial role in safeguarding the integrity and confidentiality of data transmitted between connected devices. They are essential in protecting these devices from cyber threats and ensuring secure communication across the Internet of Things ecosystem.
Importance of IoT Security Protocols
IoT security protocols are designed to establish secure connections and authenticate devices, preventing unauthorized access to sensitive information. By encrypting data and implementing secure communication channels, these protocols help mitigate the risk of data breaches and cyber attacks.
- Transport Layer Security (TLS): TLS is a widely used protocol that ensures data privacy and integrity over the network. It encrypts data during transmission, preventing eavesdropping and tampering.
- Message Queuing Telemetry Transport (MQTT): MQTT is a lightweight protocol commonly used in IoT deployments for efficient messaging between devices. It incorporates security features such as authentication and access control to protect data exchanges.
- Advanced Encryption Standard (AES): AES is a symmetric encryption algorithm utilized in IoT security to secure data at rest and in transit. It provides strong cryptographic protection against unauthorized access.
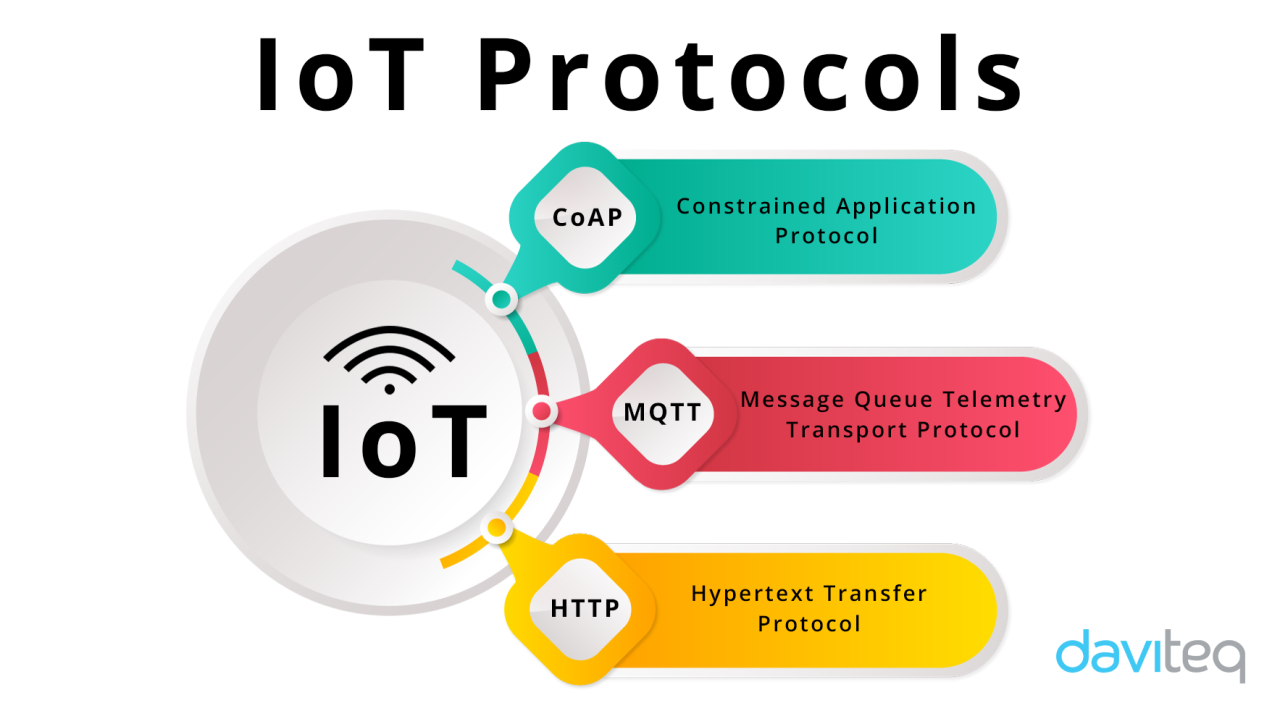
Types of IoT Security Protocols
When it comes to securing IoT devices and networks, various security protocols play a crucial role in ensuring data confidentiality, integrity, and authentication. Two common types of encryption protocols used in IoT security are symmetric and asymmetric encryption.
Symmetric vs. Asymmetric Encryption Protocols, IoT security protocols
Symmetric encryption involves using the same key for both encryption and decryption of data. This type of encryption is faster and more efficient but requires a secure way to share the key between communicating parties. On the other hand, asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption. While asymmetric encryption provides better security, it is slower due to the complexity of managing key pairs.
Transport Layer Security (TLS) Protocol
Transport Layer Security (TLS) protocol is essential for securing IoT communications by providing encryption, authentication, and data integrity. It ensures that data exchanged between IoT devices and servers is encrypted and secure, protecting it from unauthorized access and tampering. TLS plays a significant role in establishing secure connections over the internet, safeguarding sensitive information transmitted in IoT environments.
Message Queuing Telemetry Transport (MQTT) Protocol
Message Queuing Telemetry Transport (MQTT) protocol is commonly used for IoT device connectivity, enabling efficient communication between devices and servers. MQTT is a lightweight messaging protocol that facilitates the exchange of data in a publish-subscribe model, allowing devices to send and receive messages in a scalable and reliable manner. By implementing MQTT, IoT systems can achieve real-time communication and seamless integration of devices in a secure and efficient manner.
Vulnerabilities in IoT Security Protocols
IoT security protocols, like any other technology, are not immune to vulnerabilities. These weaknesses can be exploited by malicious actors to gain unauthorized access, steal sensitive data, or disrupt IoT devices and networks.
Weak Authentication Mechanisms:
One common vulnerability in IoT security protocols is the use of weak authentication mechanisms. This includes default passwords, simple PINs, or easily guessable credentials. Attackers can exploit these weak authentication methods to gain access to IoT devices and compromise the entire network.
Potential Risks of Outdated or Unsecure IoT Security Protocols:
Using outdated or unsecure IoT security protocols can pose significant risks to organizations and individuals. These protocols may lack essential security features, leaving devices vulnerable to attacks. Additionally, outdated protocols may not receive timely security updates, making them an easy target for cybercriminals.
Examples of Real-World Incidents Caused by Vulnerabilities in IoT Security Protocols:
There have been several real-world incidents caused by vulnerabilities in IoT security protocols. For instance, the Mirai botnet attack in 2016 exploited weak security on IoT devices to launch massive DDoS attacks, disrupting major websites and services. Another example is the BlueBorne vulnerability, which affected billions of IoT devices worldwide, allowing attackers to take control of these devices remotely.
Best Practices for Implementing IoT Security Protocols
Implementing IoT security protocols is crucial in ensuring the protection of connected devices and networks. Here are some best practices to consider:
Regular Software Updates and Patches
Regular software updates and patches are essential for maintaining the security of IoT devices. These updates often include security fixes for known vulnerabilities, ensuring that your devices are protected against the latest threats. It is important to stay vigilant and install updates as soon as they become available to minimize the risk of security breaches.
Secure Key Management Practices
Secure key management is vital in IoT security protocols to protect sensitive data and communications. It is important to generate strong encryption keys, securely store them, and regularly rotate keys to prevent unauthorized access. Implementing secure key management practices can help safeguard the integrity and confidentiality of data transmitted between IoT devices.
Intrusion Detection Systems
Intrusion detection systems play a crucial role in enhancing the security of IoT networks by monitoring network traffic for suspicious activity or unauthorized access attempts. By detecting and alerting on potential security threats in real-time, intrusion detection systems help organizations respond promptly to security incidents and mitigate risks. Integrating intrusion detection systems into IoT security protocols can help identify and prevent cyber attacks before they cause significant damage.
FAQ Explained
What are some common IoT security protocols?
Some common IoT security protocols include Transport Layer Security (TLS), Message Queuing Telemetry Transport (MQTT), and symmetric/asymmetric encryption protocols.
How important is regular software updates for IoT security?
Regular software updates are crucial for maintaining the security of IoT devices as they often contain patches to fix vulnerabilities.
What risks are associated with using outdated IoT security protocols?
Using outdated IoT security protocols can expose devices to potential cyber threats and compromise data integrity.