Data Breach Prevention Measures
Data breach prevention measures are essential in today’s digital landscape to protect sensitive information. As organizations face increasing cybersecurity threats, implementing robust measures is crucial to mitigate risks and safeguard valuable data. From common prevention techniques to employee training and incident response planning, this overview delves into the key aspects of keeping your data secure.
Importance of Data Breach Prevention Measures

In today’s digital age, data breach prevention measures are essential for organizations to safeguard sensitive information and maintain trust with their customers. Without adequate protection, businesses are at risk of facing severe consequences that can impact their reputation, finances, and overall operations.
Data breaches can lead to a multitude of negative outcomes for organizations. One of the most significant consequences is the loss of customer trust and loyalty. When personal data is compromised, customers may feel betrayed and choose to take their business elsewhere, resulting in a loss of revenue and potential legal implications.
Furthermore, data breaches can have a devastating financial impact on businesses. The costs associated with investigating the breach, notifying affected individuals, implementing security upgrades, and potential legal fees can add up quickly. In addition, organizations may face fines and penalties for non-compliance with data protection regulations, further exacerbating the financial strain.
It is crucial for organizations to prioritize data breach prevention measures to mitigate these risks and protect their valuable assets. By investing in robust cybersecurity measures, conducting regular risk assessments, and educating employees on best practices, businesses can minimize the likelihood of a data breach and safeguard their reputation and bottom line.
Common Data Breach Prevention Techniques: Data Breach Prevention Measures
Data breaches can have serious consequences for businesses and individuals, making it crucial to implement effective prevention measures. Here are some common techniques used to prevent data breaches:
Role of Encryption
Encryption plays a vital role in data breach prevention by converting sensitive information into a code that can only be deciphered with the correct key. This ensures that even if unauthorized parties gain access to the data, they cannot read or use it without the encryption key. By encrypting data both at rest and in transit, organizations can add an extra layer of security to protect their information.
Importance of Access Control
Access control is another critical component of data breach prevention, as it helps limit the exposure of sensitive data to only authorized individuals. By implementing strict access control measures, such as user authentication, role-based access, and least privilege principles, organizations can reduce the risk of unauthorized access and potential data breaches. Monitoring and logging access activities can also help detect any unusual behavior that may indicate a security threat.
Employee Training and Awareness
Training employees on data security best practices is crucial in preventing data breaches. By raising awareness about the importance of protecting sensitive information, employees become more vigilant and proactive in safeguarding data. Employee accountability plays a significant role in ensuring data security measures are followed consistently throughout the organization.
Effective Strategies for Raising Awareness
- Conduct regular security training sessions to educate employees on the latest data breach prevention techniques and protocols.
- Implement phishing simulation exercises to test employees’ ability to identify and report suspicious emails or messages.
- Create engaging and informative posters, newsletters, and emails to reinforce data security best practices and remind employees of their role in preventing breaches.
Role of Employee Accountability
- Encourage employees to report any security incidents or concerns promptly to the designated IT or security team.
- Establish clear guidelines and consequences for non-compliance with data security policies to emphasize the importance of following security protocols.
- Empower employees to take ownership of their role in protecting sensitive data and promote a culture of accountability throughout the organization.
Regular Data Security Audits and Assessments
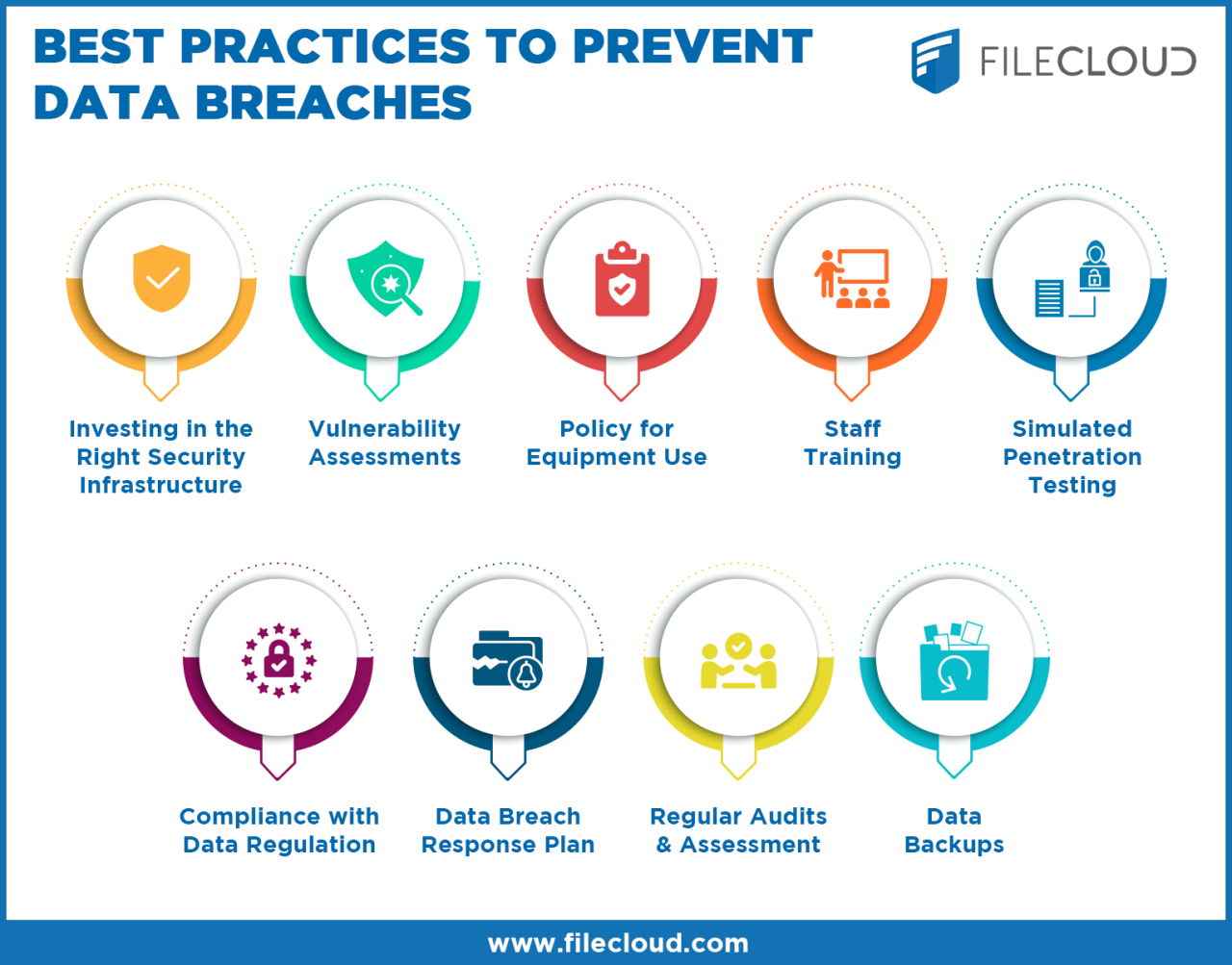
Regular data security audits and assessments are crucial in maintaining the integrity of your organization’s data and preventing potential breaches. By regularly reviewing and evaluating your security measures, you can identify vulnerabilities and weaknesses before they are exploited by malicious actors.
Importance of Conducting Regular Security Audits
- Regular audits help in identifying potential vulnerabilities in your systems and processes.
- It allows you to stay proactive in addressing security issues before they escalate.
- Helps in ensuring compliance with industry regulations and standards.
Step-by-Step Guide on Performing a Data Security Assessment
- Start by defining the scope of the assessment, including the systems and data to be reviewed.
- Conduct a vulnerability scan to identify any weaknesses in your network and applications.
- Perform penetration testing to simulate real-world attacks and identify potential entry points for hackers.
- Analyze the results and prioritize the identified risks based on their potential impact.
- Develop a remediation plan to address the identified vulnerabilities and enhance your security measures.
Benefits of Third-Party Assessments in Evaluating Data Breach Prevention Measures
- Third-party assessments provide an unbiased evaluation of your security posture.
- Brings in external expertise and perspective to identify blind spots that internal teams may overlook.
- Helps in validating the effectiveness of your existing security controls and measures.
- Enhances credibility and trust with stakeholders by demonstrating a commitment to data security.
Incident Response Planning

Incident response planning is a crucial aspect of data breach prevention, as it lays out a structured approach to handling security incidents effectively. It involves preparing for, managing, and recovering from security breaches to minimize damage and ensure business continuity.
Components of an Effective Incident Response Plan
An effective incident response plan typically includes the following components:
- Incident detection and identification procedures
- Response team roles and responsibilities
- Communication and notification protocols
- Containment, eradication, and recovery processes
- Post-incident analysis and documentation
Importance of Testing Incident Response Plans Regularly
Regular testing of incident response plans is essential to ensure their effectiveness in real-world scenarios. Testing helps identify weaknesses, improve response times, and enhance coordination among response team members. It also provides an opportunity to update and refine the plan based on lessons learned from each exercise.
Best Practices for Responding to a Data Breach Incident
- Act Quickly: Time is of the essence in responding to a data breach. Prompt action can help contain the incident and minimize its impact.
- Notify Stakeholders: Keep all relevant stakeholders informed about the breach, including customers, employees, and regulatory authorities.
- Preserve Evidence: Document all activities related to the incident, including evidence collection, to support any legal or regulatory requirements.
- Engage Experts: Consider involving cybersecurity experts or legal counsel to assist in the response process and ensure compliance with data protection laws.
- Review and Improve: After the incident is resolved, conduct a thorough review to identify areas for improvement in the incident response plan.
FAQ Corner
Why are data breach prevention measures important?
Data breach prevention measures are crucial as they help organizations protect sensitive data, maintain trust with customers, and avoid costly security incidents.
What are some common data breach prevention techniques?
Common techniques include encryption, access control, regular security audits, and incident response planning.
How can employee training help in data breach prevention?
Employee training ensures that staff are aware of best practices, reducing the likelihood of human error leading to data breaches.
Why is incident response planning important?
Having an effective incident response plan in place helps organizations minimize the impact of a data breach and respond swiftly to mitigate further damage.