Cybersecurity Risk Assessments
Cybersecurity risk assessments set the stage for protecting organizational assets from digital threats. From understanding the importance to exploring different types and processes, this topic delves into the critical realm of cybersecurity.
As organizations increasingly rely on digital infrastructure, the need for robust risk assessments becomes paramount. Let’s explore the world of cybersecurity risk assessments and how they play a crucial role in safeguarding against cyber threats.
Importance of Cybersecurity Risk Assessments
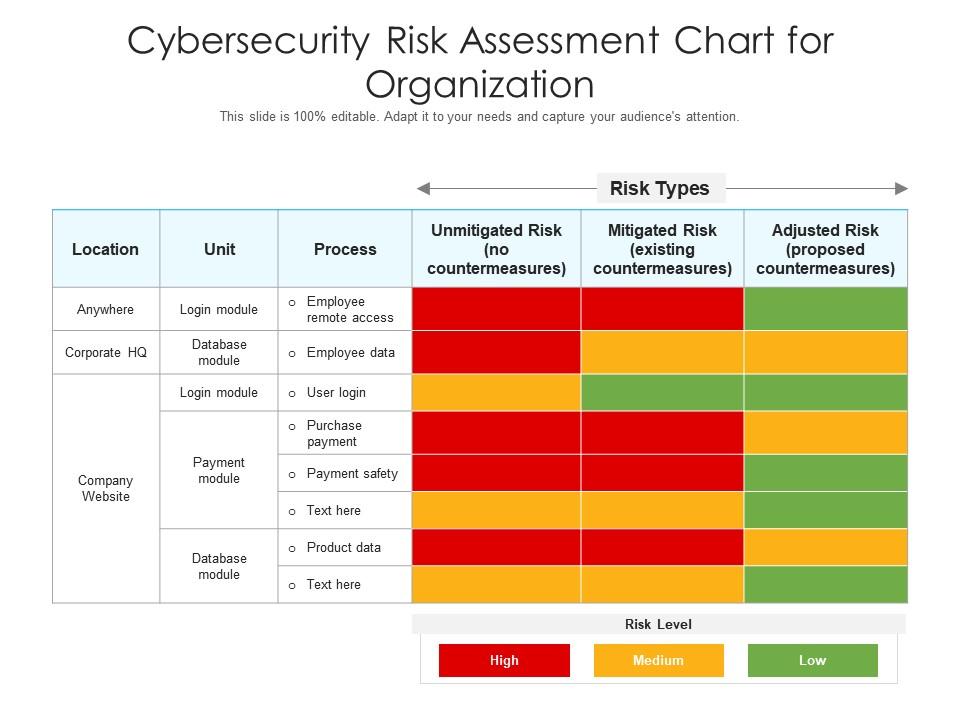
Cybersecurity risk assessments are crucial for organizations to ensure the protection of sensitive data, systems, and networks from potential threats. By conducting regular risk assessments, companies can proactively identify vulnerabilities and implement necessary measures to prevent cyber attacks.
Consequences of Not Conducting Regular Risk Assessments
- Increased likelihood of data breaches and loss of confidential information.
- Potential financial losses due to cyber attacks and legal repercussions.
- Damage to reputation and loss of customer trust.
Identification and Mitigation of Vulnerabilities
Risk assessments help organizations in identifying weak points in their cybersecurity infrastructure and developing strategies to mitigate these vulnerabilities.
Types of Cybersecurity Risk Assessments
When it comes to cybersecurity risk assessments, there are different types that organizations can utilize to identify and mitigate potential threats. These assessments help in understanding the vulnerabilities and risks that may impact the security of systems and data.
Quantitative vs. Qualitative Assessments
- Quantitative Assessments: These assessments involve assigning numerical values to risks based on factors such as financial loss, probability of occurrence, and potential impact. This approach helps in prioritizing risks based on their severity and likelihood.
- Qualitative Assessments: Unlike quantitative assessments, qualitative assessments focus more on descriptive analysis rather than numerical values. This method helps in understanding the nature of risks, their potential consequences, and the overall impact on the organization.
Internal vs. External Risk Assessments
- Internal Risk Assessments: Internal risk assessments are conducted by the organization’s own security team or a third-party security provider hired by the organization. These assessments focus on identifying risks within the organization’s infrastructure, systems, and processes.
- External Risk Assessments: External risk assessments are conducted by independent cybersecurity firms or consultants from outside the organization. These assessments simulate real-world cyber threats and attacks to identify vulnerabilities that could be exploited by external malicious actors.
Examples of Scenarios
- Quantitative assessments are most suitable for financial institutions that need to prioritize risks based on potential financial losses.
- Qualitative assessments are ideal for organizations that prioritize understanding the nature of risks and their potential impact on business operations.
- Internal risk assessments are beneficial for organizations looking to improve their internal security posture and identify vulnerabilities within their systems.
- External risk assessments are essential for organizations with high-value assets and sensitive data that are at risk of external cyber threats.
Process of Conducting Cybersecurity Risk Assessments
Conducting a cybersecurity risk assessment is a crucial step in safeguarding an organization’s digital assets and information. It involves a systematic approach to identifying, analyzing, and evaluating potential risks that could compromise the security of the organization.
Steps Involved in Conducting a Cybersecurity Risk Assessment
- Identify Assets: Begin by identifying all the digital assets within the organization that need to be protected, including hardware, software, data, and networks.
- Identify Threats: Determine the potential threats that could exploit vulnerabilities in the system and compromise the security of the assets.
- Assess Vulnerabilities: Conduct a thorough assessment to identify weaknesses or vulnerabilities in the system that could be targeted by threats.
- Analyze Risks: Evaluate the likelihood of threats exploiting vulnerabilities and the potential impact it could have on the organization.
- Develop Mitigation Strategies: Create a plan to mitigate the identified risks by implementing security controls and measures.
- Monitor and Review: Continuously monitor the effectiveness of the mitigation strategies and regularly review the risk assessment process to ensure ongoing protection.
Role of Stakeholders in the Assessment Process
Stakeholders play a vital role in the cybersecurity risk assessment process by providing valuable insights and expertise in their respective areas. Their involvement ensures that all aspects of the organization’s operations are considered, and relevant risks are identified and addressed effectively.
Prioritizing Risks Based on Likelihood and Impact
- Likelihood: Assess the probability of each identified risk occurring based on historical data, industry trends, and expert knowledge.
- Impact: Evaluate the potential consequences of each risk materializing, including financial losses, reputational damage, legal implications, and operational disruptions.
- Prioritization: Rank risks based on a combination of their likelihood and impact, focusing on those with the highest risk exposure to allocate resources effectively.
- Risk Treatment: Develop risk treatment plans for high-priority risks, implementing controls to reduce the likelihood of occurrence or minimize the impact if realized.
Tools and Technologies for Cybersecurity Risk Assessments
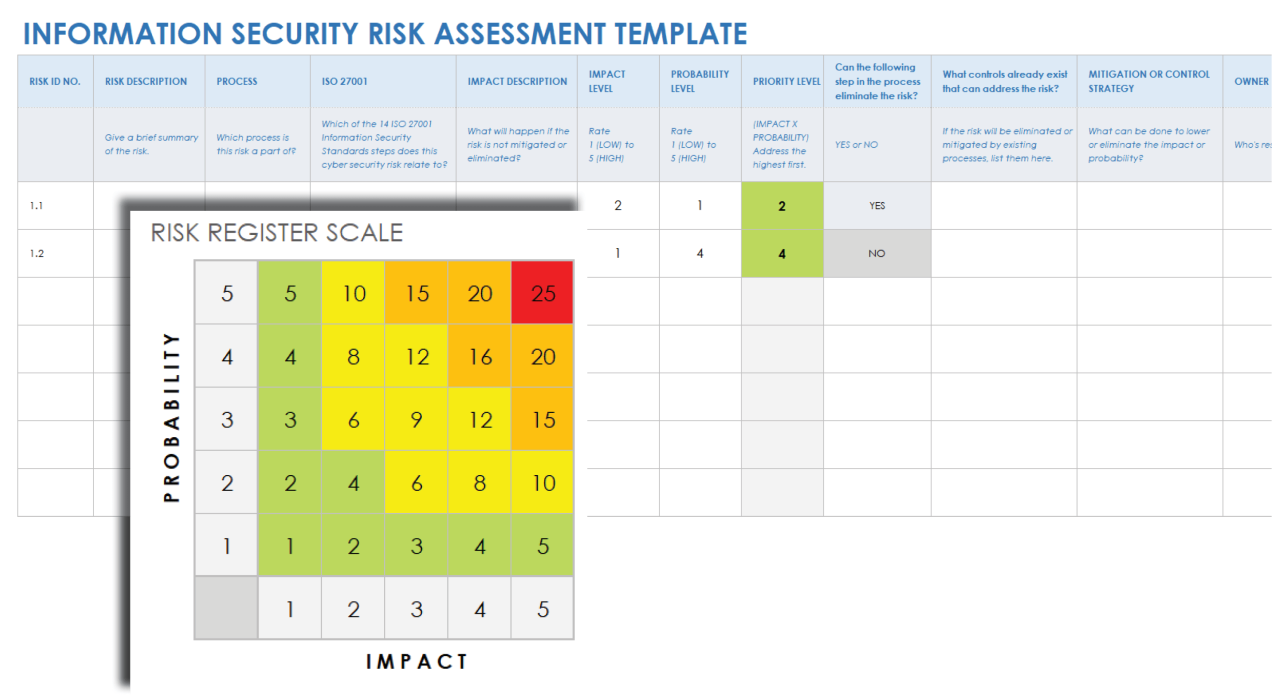
When it comes to conducting cybersecurity risk assessments, there are various tools and technologies available to help organizations identify, analyze, and mitigate potential risks. These tools play a crucial role in ensuring the security of sensitive data and systems.
Automated Vulnerability Scanners, Cybersecurity risk assessments
Automated vulnerability scanners are commonly used in cybersecurity risk assessments to identify weaknesses and vulnerabilities in networks, applications, and systems. These tools scan the infrastructure for known security flaws and provide detailed reports on potential risks.
- Nessus: A popular vulnerability scanner that helps organizations identify and prioritize security issues.
- OpenVAS: An open-source vulnerability scanner that offers a comprehensive assessment of network security.
Security Information and Event Management (SIEM) Systems
SIEM systems play a crucial role in cybersecurity risk assessments by collecting, analyzing, and correlating security event data in real-time. These platforms help organizations detect and respond to security incidents effectively.
- Splunk: A leading SIEM platform that provides real-time visibility into security events and threats.
- IBM QRadar: A comprehensive SIEM solution that helps organizations monitor security incidents and comply with regulations.
Security Risk Assessment Software
Security risk assessment software is designed to streamline the risk assessment process by providing tools for risk identification, analysis, and mitigation. These platforms help organizations prioritize security measures based on the level of risk.
- RSAM: A risk management platform that enables organizations to assess, track, and mitigate security risks effectively.
- Archer: A GRC platform that helps organizations manage risks, compliance, and audits in a unified environment.
FAQ Compilation
Why are cybersecurity risk assessments important?
Cybersecurity risk assessments are crucial as they help organizations identify vulnerabilities and mitigate potential threats before they escalate.
What are the consequences of not conducting regular risk assessments?
Not conducting regular risk assessments can leave organizations exposed to cyber threats, leading to data breaches, financial losses, and damage to reputation.
How do risk assessments help in identifying and mitigating vulnerabilities?
Risk assessments provide a structured approach to identifying weak points in security systems and taking proactive measures to address them effectively.
What are the different types of cybersecurity risk assessments?
Cybersecurity risk assessments can be quantitative or qualitative, each offering unique insights into the security posture of an organization.
How can stakeholders contribute to the cybersecurity risk assessment process?
Stakeholders play a vital role in risk assessments by providing domain-specific knowledge and insights that can enhance the overall assessment process.







