Cryptocurrency Wallet Security
Cryptocurrency wallet security is paramount in the world of digital assets, protecting your investments from potential threats. Let’s delve into the key aspects of securing your cryptocurrency wallets to ensure peace of mind and financial safety.
From understanding the importance of secure wallets to exploring best practices and common threats, this comprehensive guide will equip you with the knowledge needed to navigate the complex landscape of cryptocurrency security.
Importance of Cryptocurrency Wallet Security
Ensuring the security of your cryptocurrency wallet is paramount in the digital asset space. With the rise of cyber threats and hacking incidents, safeguarding your funds against unauthorized access is crucial to protect your investments.
Risks Associated with Insecure Wallets
- Phishing Attacks: Hackers may use deceptive emails or websites to trick users into revealing their wallet credentials, leading to theft of funds.
- Malware: Malicious software can infect devices and steal private keys or seed phrases, giving hackers access to the wallet.
- Exchange Vulnerabilities: Storing funds on exchanges exposes users to the risk of platform breaches and hacks.
Implications of Compromised Wallet Security
- Loss of Funds: A compromised wallet can result in the loss of all assets stored within, with little to no chance of recovery.
- Identity Theft: Hackers gaining access to personal information through security breaches can lead to identity theft and further financial harm.
- Damaged Reputation: In the event of a security breach, users may lose trust in the platform or service, affecting its credibility and reputation.
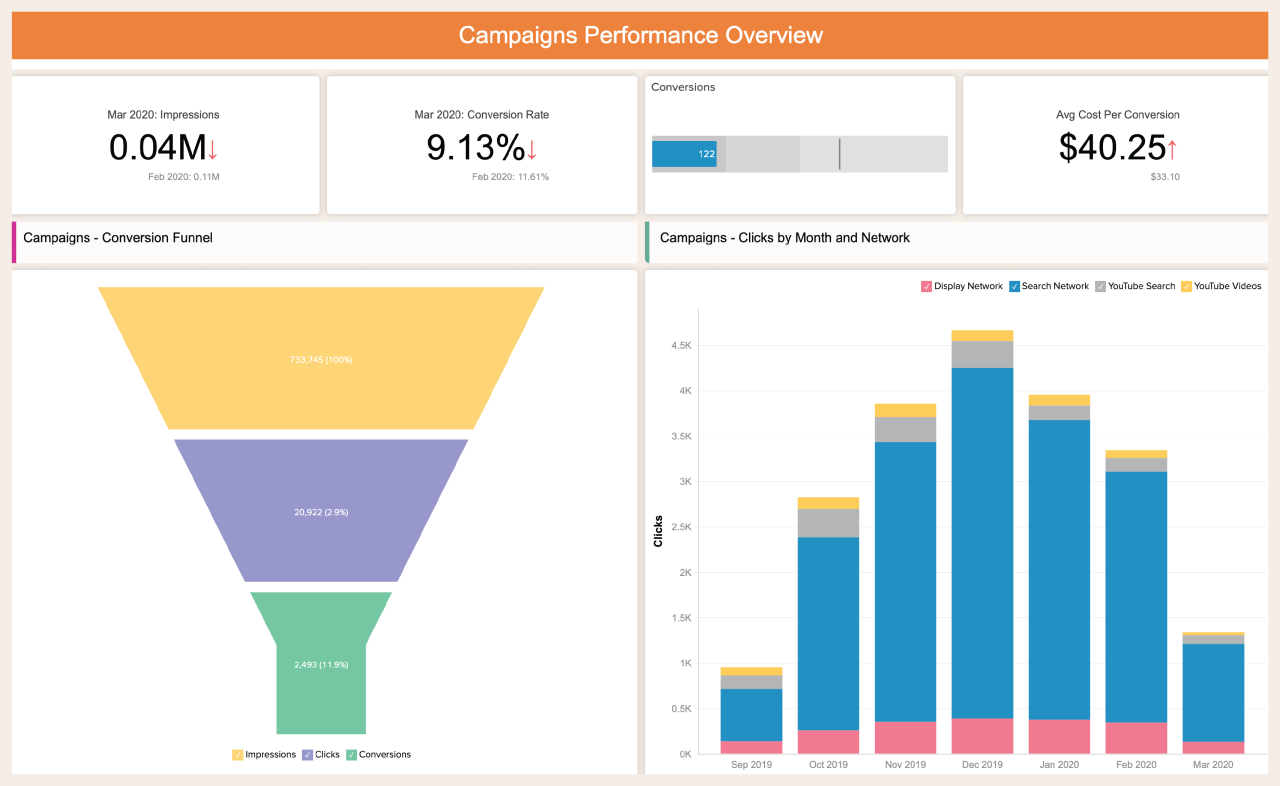
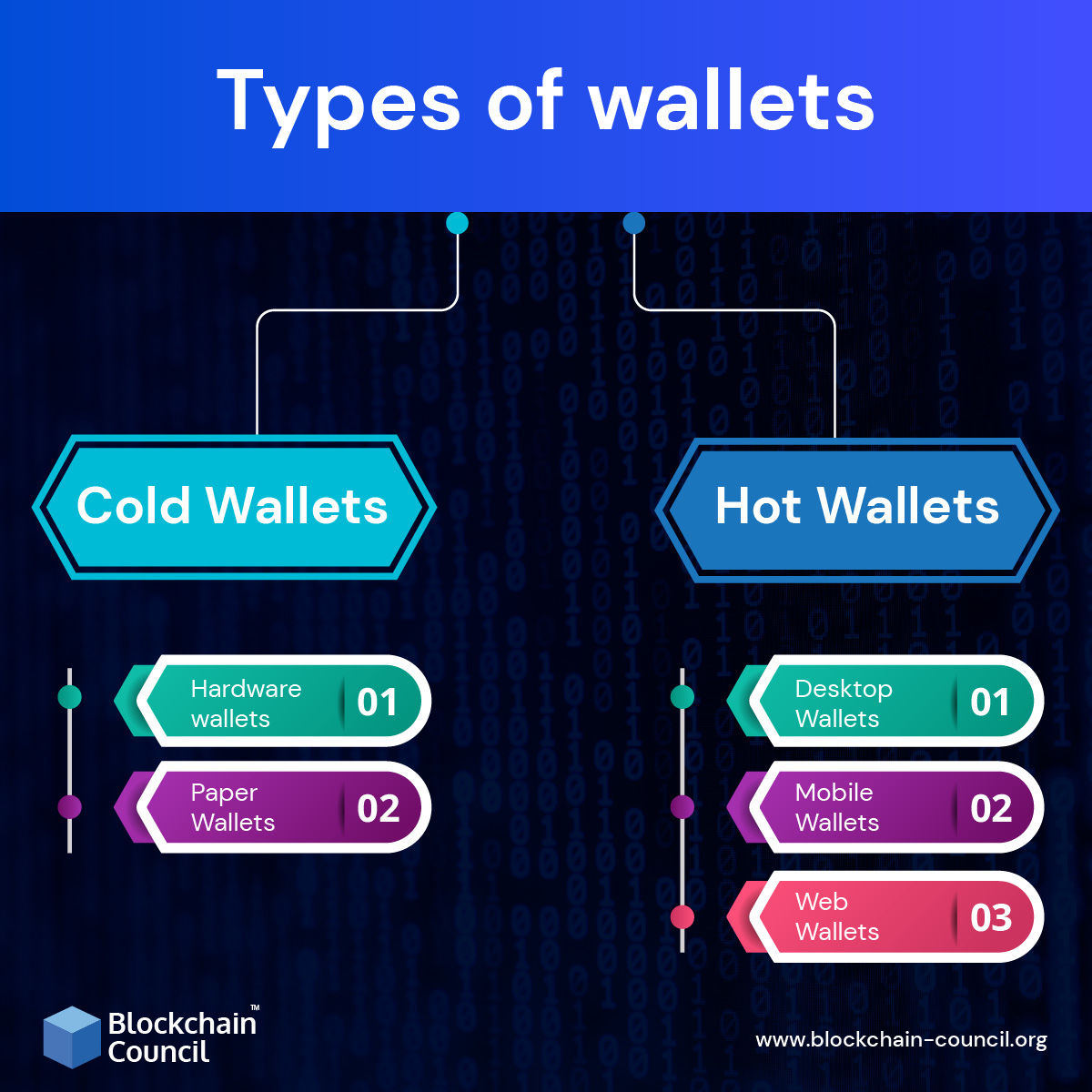
Types of Cryptocurrency Wallets
When it comes to storing your cryptocurrency, there are several types of wallets you can choose from. Each type has its own set of features, security measures, and vulnerabilities.
Hardware Wallets, Cryptocurrency wallet security
Hardware wallets are physical devices that store your cryptocurrency offline, making them highly secure against online hacking attempts. These wallets are considered one of the safest options for storing your digital assets.
- They are immune to computer viruses and malware.
- Require physical access to the device to conduct transactions.
- Usually come with backup and recovery options in case the device is lost or damaged.
Software Wallets
Software wallets are applications or programs that you can install on your computer or mobile device to store your cryptocurrency. While convenient, they are more vulnerable to online attacks compared to hardware wallets.
- Can be accessed from anywhere with an internet connection.
- May store private keys on the device, making them susceptible to hacking.
- Users are responsible for securing their devices and ensuring they are free from malware.
Paper Wallets
Paper wallets involve printing out your private and public keys on a piece of paper, which is then stored in a secure location. While offline and secure from online attacks, paper wallets are susceptible to physical damage or loss.
- Highly secure as they are not connected to the internet.
- Require careful handling to prevent loss or damage to the paper.
- Not easily accessible for regular transactions, as they need to be imported into a digital wallet first.
Best Practices for Securing Cryptocurrency Wallets
Cryptocurrency wallets store your digital assets, making them a prime target for hackers. To ensure the safety of your funds, it is crucial to follow best practices for securing your cryptocurrency wallet.
Use Strong Passwords and Two-Factor Authentication
When setting up your cryptocurrency wallet, always use a strong, unique password that includes a combination of letters, numbers, and special characters. Avoid using easily guessable passwords like “123456” or “password.” Additionally, enable two-factor authentication (2FA) for an extra layer of security. 2FA requires you to provide a second piece of information, such as a code sent to your phone, when logging in to your wallet.
Backup Your Wallet
Make sure to regularly backup your wallet’s private keys or seed phrase. This backup will allow you to recover your funds in case your wallet is lost, stolen, or damaged. Store your backup in a secure location, such as a safe deposit box or a encrypted USB drive.
Keep Your Wallet Software Updated
Always keep your cryptocurrency wallet software up to date. Developers frequently release updates to patch security vulnerabilities and improve overall performance. By staying current with software updates, you can protect your wallet from potential threats.
Use Cold Storage for Long-Term Holdings
Consider using cold storage solutions, such as hardware wallets or paper wallets, for storing large amounts of cryptocurrency over the long term. Cold storage wallets are not connected to the internet, making them less vulnerable to hacking attempts compared to hot wallets.
Be Cautious of Phishing Attacks
Be vigilant against phishing attacks, where scammers try to trick you into revealing your wallet credentials. Avoid clicking on unsolicited links or providing sensitive information to unknown sources. Always verify the authenticity of the website or email before sharing any personal information.
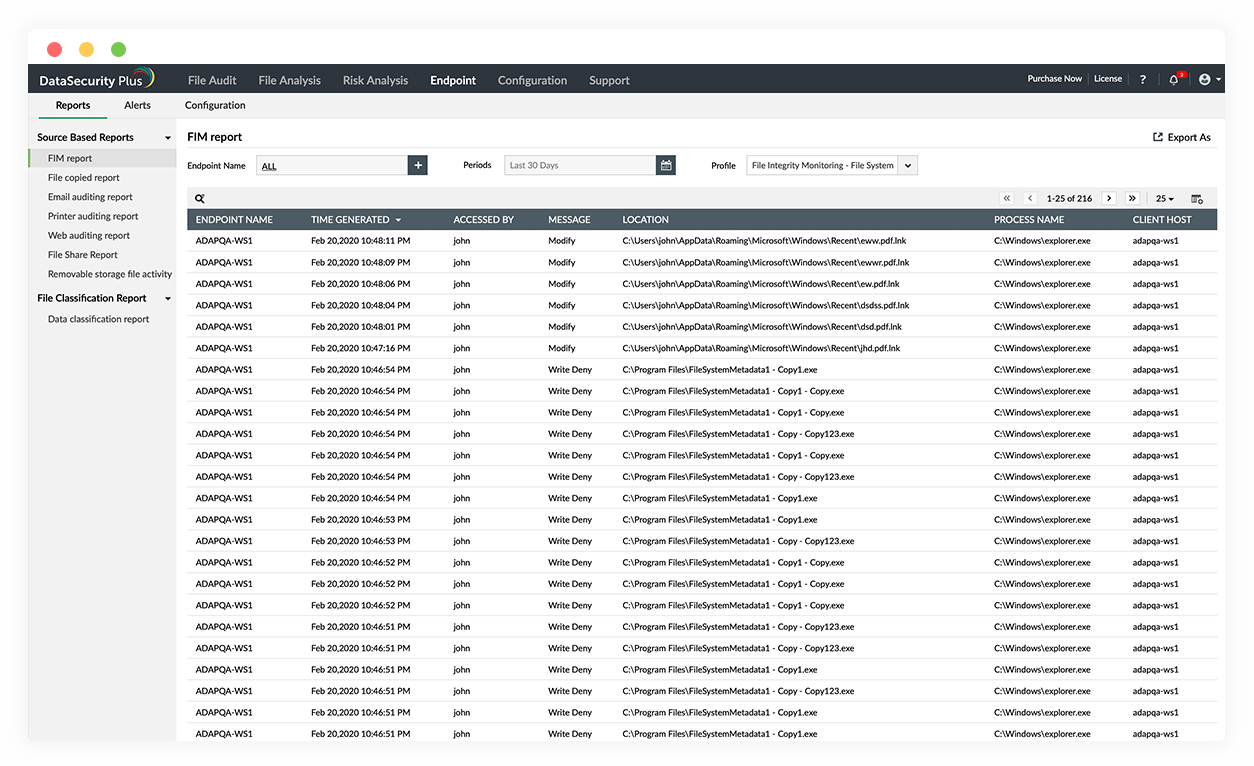
Regularly Monitor Your Account Activity
Monitor your cryptocurrency wallet regularly for any unauthorized transactions or suspicious activity. By staying vigilant and reviewing your account activity, you can quickly detect any potential security breaches and take appropriate action to protect your funds.
Common Threats to Cryptocurrency Wallet Security

Cryptocurrency wallet users face various threats that can compromise the security of their digital assets. It is crucial to be aware of these threats to take necessary precautions and protect your funds.
Phishing Attacks
Phishing attacks are a common threat to cryptocurrency wallet security, where malicious actors attempt to deceive users into providing sensitive information such as private keys or login credentials. These attacks often involve fraudulent emails, websites, or messages that mimic legitimate sources to trick users into disclosing their valuable data. It is essential to always verify the authenticity of communication and avoid clicking on suspicious links to prevent falling victim to phishing scams.
Malware
Malware poses a significant risk to cryptocurrency wallets by infecting devices and compromising security. Malicious software can steal private keys, seed phrases, and other sensitive information stored on the device, allowing attackers to gain unauthorized access to the wallet and transfer funds. To mitigate the risk of malware attacks, users should regularly update their antivirus software, avoid downloading files from unknown sources, and secure their devices with strong passwords.
Recovery and Backup Procedures for Cryptocurrency Wallets: Cryptocurrency Wallet Security

Ensuring proper backup procedures for your cryptocurrency wallet is crucial in case of loss or theft. Without a backup, you risk losing access to your funds permanently.
Importance of Backup Procedures
Backing up your cryptocurrency wallet is like creating a safety net for your digital assets. It provides you with a way to recover your funds in case your wallet is compromised or inaccessible.
- Always backup your wallet immediately after creating it or making any significant changes.
- Regularly update your backup to include new transactions or changes in your wallet.
- Store your backup in multiple secure locations to minimize the risk of loss.
How to Safely Backup and Recover a Cryptocurrency Wallet
Follow these steps to safely backup and recover your cryptocurrency wallet:
- Create a secure offline backup of your wallet’s private keys or seed phrase.
- Encrypt your backup with a strong password to prevent unauthorized access.
- Test your backup by restoring your wallet on a different device to ensure it works correctly.
Best Practices for Storing Backup Information Securely
It’s essential to store your backup information securely to prevent unauthorized access to your funds:
- Avoid storing backup files on cloud storage or online platforms that are vulnerable to hacking.
- Use encrypted USB drives or hardware wallets to store your backup offline.
- Consider using a safe deposit box or a secure location at home to store physical backups.
User Queries
What are the risks of insecure wallets?
Insecure wallets can lead to theft of your digital assets, unauthorized access, and potential loss of funds.
How can users protect their wallets?
Users can enhance wallet security by using strong passwords, enabling two-factor authentication, and keeping their private keys secure.
What are the common threats to cryptocurrency wallet security?
Common threats include phishing attacks, malware, and unauthorized access to wallets through various means.